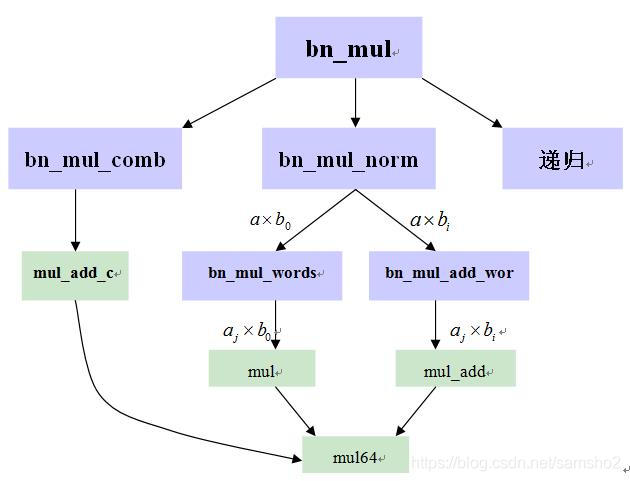
大整数乘法
基线算法
使用 双精度 中间变量,算法复杂度 $O(n^2)$,进位累加次数 $n*n$
Comba 算法
使用 三精度 中间变量,算法复杂度 $O(n^2)$,进位累加次数 $2*n$
Karatsuba 算法
使用 分而治之 思想,算法复杂度 $O(n^{log_23}) \approx O(n^{1.585})$
Montgomery 算法(蒙哥马利算法)
快速计算模乘、模幂运算(蒙哥马利算法)
大数库
-
MIRACL Cryptographic SDK: Multiprecision Integer and Rational Arithmetic Cryptographic Library is a C software library that is widely regarded by developers as the gold standard open source SDK for elliptic curve cryptography (ECC).
针对椭圆曲线进行优化
-
GMP is a free library for arbitrary precision arithmetic, operating on signed integers, rational numbers, and floating-point numbers. There is no practical limit to the precision except the ones implied by the available memory in the machine GMP runs on. GMP has a rich set of functions, and the functions have a regular interface.
主要用于整数、有理数和浮点数运算,针对椭圆曲线支持较少
-
包含大数库
测试
SM2-Sign 中的关键步骤为 $k*G$,其中 $G$ 为椭圆曲线生成元。由于椭圆曲线参数是确定的,因此可针对 $G$ 预先生成查找表,从而加速点乘运算。
SM2-Verify 中的关键步骤为 $s^{\prime}G + r^{\prime}P$, 由于 $P$ 为用户公钥,是可变参数,因此无法针对 $r^{\prime}*P$ 预先生成查找表,只能在验签过程中实时计算部分查找表加速验签过程。
SM2-GmSSL
不预先生成查找表(no
EC_KEY_precompute_mult)wang@ubuntu:~/project/sm2-base$ ./main
verify speed: 722.662287/s
test gmssl sm2 speed in 10s
sm2 verify count: 8176.000
time cost: 11.314test gmssl sm2 verify speed in 10s
verify speed: 617.263539/s
gmssl sm2 verify count: 8176.000
time cost: 13.246预先生成乘法查找表(
EC_KEY_precompute_mult)test gmssl sm2 speed in 10s
verify speed: 3603.007366/s
sm2 verify count: 65520.000
time cost: 18.185test gmssl sm2 verify speed in 10s
verify speed: 637.009360/s
gmssl sm2 verify count: 8176.000
time cost: 12.835
wang@ubuntu:~$ gmssl speed sm2
sign verify sign/s verify/s
<font color=red>256 bit sm2 (sm2p256v1) 0.0003s 0.0015s 3601.3 668.8</font>
最新版
两个查找表—关闭
SM2_NO_CONST_TIME
GmSSL 2.1.0 - OpenSSL 1.1.0d 03 Jan 2018
built on: reproducible build, date unspecified
options:bn(64,64) rc4(char) des(int) aes(partial) idea(int) blowfish(ptr)
compiler: gcc -DDSO_DLFCN -DHAVE_DLFCN_H -DNDEBUG -DOPENSSL_THREADS -DOPENSSL_NO_STATIC_ENGINE -DOPENSSL_PIC -DOPENSSL_BN_ASM_MONT -DSHA1_ASM -DSHA256_ASM -DSHA512_ASM -DVPAES_ASM -DECP_NISTZ256_ASM -DPOLY1305_ASM -DGMSSL_NO_TURBO -DOPENSSLDIR=”\”/home/wang/local/gmssl\”” -DENGINESDIR=”\”/home/wang/local/gmssl/lib/engines-1.1\”” -Wa,—noexecstacksign verify sign/s verify/s256 bit sm2 (sm2p256v1) 0.0002s 0.0008s 5196.5 1306.8
encrypt decrypt enc/s dec/s256 bit sm2 (sm2p256v1) 0.0009s 0.0007s 1165.1 1397.3
两个查找表—开启
SM2_NO_CONST_TIME
GmSSL 2.1.0 - OpenSSL 1.1.0d 03 Jan 2018
built on: reproducible build, date unspecified
options:bn(64,64) rc4(char) des(int) aes(partial) idea(int) blowfish(ptr)
compiler: gcc -DDSO_DLFCN -DHAVE_DLFCN_H -DNDEBUG -DOPENSSL_THREADS -DOPENSSL_NO_STATIC_ENGINE -DOPENSSL_PIC -DOPENSSL_BN_ASM_MONT -DSHA1_ASM -DSHA256_ASM -DSHA512_ASM -DVPAES_ASM -DECP_NISTZ256_ASM -DPOLY1305_ASM -DSM2_NO_CONST_TIME -DGMSSL_NO_TURBO -DOPENSSLDIR=”\”/home/wang/local/gmssl\”” -DENGINESDIR=”\”/home/wang/local/gmssl/lib/engines-1.1\”” -Wa,—noexecstacksign verify sign/s verify/s256 bit sm2 (sm2p256v1) 0.0002s 0.0008s 5203.7 1331.6
encrypt decrypt enc/s dec/s256 bit sm2 (sm2p256v1) 0.0009s 0.0007s 1160.1 1423.
SM2默认曲线——使用NISTP查表(关闭
ec_nistp_64_gcc_128, 开启SM2_NO_CONST_TIME)GmSSL 2.5.4 - OpenSSL 1.1.0d 19 Jun 2019
built on: reproducible build, date unspecified
options:bn(64,64) rc4(char) des(int) aes(partial) idea(int) blowfish(ptr)
compiler: gcc -DDSO_DLFCN -DHAVE_DLFCN_H -DNDEBUG -DOPENSSL_THREADS -DOPENSSL_NO_STATIC_ENGINE -DOPENSSL_PIC -DOPENSSL_BN_ASM_MONT -DSHA1_ASM -DSHA256_ASM -DSHA512_ASM -DVPAES_ASM -DECP_NISTZ256_ASM -DPOLY1305_ASM -DSM2_NO_CONST_TIME -DGMSSL_NO_TURBO -DOPENSSLDIR=”\”/home/wang/local/gmssl\”” -DENGINESDIR=”\”/home/wang/local/gmssl/lib/engines-1.1\”” -Wa,—noexecstacksign verify sign/s verify/s256 bit sm2 (sm2p256v1) 0.0002s 0.0007s 6457.7 1340.3
encrypt decrypt enc/s dec/s256 bit sm2 (sm2p256v1) 0.0008s 0.0007s 1190.5 1406.4
SM2默认曲线——使用SM2P256查表(开启
ec_nistp_64_gcc_128, 开启SM2_NO_CONST_TIME)GmSSL 2.5.4 - OpenSSL 1.1.0d 19 Jun 2019
built on: reproducible build, date unspecified
options:bn(64,64) rc4(char) des(int) aes(partial) idea(int) blowfish(ptr)
compiler: gcc -DDSO_DLFCN -DHAVE_DLFCN_H -DNDEBUG -DOPENSSL_THREADS -DOPENSSL_NO_STATIC_ENGINE -DOPENSSL_PIC -DOPENSSL_BN_ASM_MONT -DSHA1_ASM -DSHA256_ASM -DSHA512_ASM -DVPAES_ASM -DECP_NISTZ256_ASM -DPOLY1305_ASM -DL_ENDIAN -D__arch64__ -DSM2_NO_CONST_TIME -DGMSSL_NO_TURBO -DOPENSSLDIR=”\”/home/wang/local/gmssl\”” -DENGINESDIR=”\”/home/wang/local/gmssl/lib/engines-1.1\”” -Wa,—noexecstacksign verify sign/s verify/s256 bit sm2 (sm2p256v1) 0.0001s 0.0004s 7275.6 2594.0
encrypt decrypt enc/s dec/s256 bit sm2 (sm2p256v1) 0.0007s 0.0006s 1394.6 1691.9
SM2默认曲线——32个查找表(开启
ec_nistp_64_gcc_128, 开启SM2_NO_CONST_TIME, 开启SM2P256TABLE)GmSSL 2.5.4 - OpenSSL 1.1.0d 19 Jun 2019
built on: reproducible build, date unspecified
options:bn(64,64) rc4(char) des(int) aes(partial) idea(int) blowfish(ptr)
compiler: gcc -DDSO_DLFCN -DHAVE_DLFCN_H -DNDEBUG -DOPENSSL_THREADS -DOPENSSL_NO_STATIC_ENGINE -DOPENSSL_PIC -DOPENSSL_BN_ASM_MONT -DSHA1_ASM -DSHA256_ASM -DSHA512_ASM -DVPAES_ASM -DECP_NISTZ256_ASM -DPOLY1305_ASM -DSM2P256TABLE -DL_ENDIAN -D__arch64__ -DSM2_NO_CONST_TIME -DGMSSL_NO_TURBO -DOPENSSLDIR=”\”/home/wang/local/gmssl\”” -DENGINESDIR=”\”/home/wang/local/gmssl/lib/engines-1.1\”” -Wa,—noexecstacksign verify sign/s verify/s256 bit sm2 (sm2p256v1) 0.0001s 0.0003s 12838.6 2915.4
encrypt decrypt enc/s dec/s256 bit sm2 (sm2p256v1) 0.0007s 0.0006s 1512.6 1718.2
1 | gmssl ecparam -text -noout -name sm2p256v1 -param_enc explicit |
对于 P256 上的一个点 x,其大小为 256 bits = 32 bytes = 8 words = 4 dwords,对于定义在 P256 上的椭圆曲线点 G=(Gx, Gy),其大小为 8 dwords。考虑 $k*G$:
1 | /*- |
1 |
|
GmSSL SM2 依赖项
wang@ubuntu:~/project/sm2-base$ gcc -M sm2test.c | grep openssl
/usr/local/include/openssl/bn.h /usr/local/include/openssl/e_os2.h \
/usr/local/include/openssl/opensslconf.h /usr/include/inttypes.h \
/usr/local/include/openssl/ossl_typ.h \
/usr/local/include/openssl/crypto.h /usr/include/time.h \
/usr/local/include/openssl/stack.h \
/usr/local/include/openssl/safestack.h \
/usr/local/include/openssl/opensslv.h \
/usr/local/include/openssl/symhacks.h /usr/include/pthread.h \
/usr/local/include/openssl/ec.h /usr/local/include/openssl/asn1.h \
/usr/local/include/openssl/bio.h /usr/local/include/openssl/evp.h \
/usr/local/include/openssl/objects.h \
/usr/local/include/openssl/obj_mac.h /usr/local/include/openssl/rand.h \
/usr/local/include/openssl/sm2.h /usr/local/include/openssl/err.h \
/usr/local/include/openssl/lhash.h /usr/include/errno.h \
/usr/local/include/openssl/kdf2.h /usr/local/include/openssl/kdf.h \
/usr/local/include/openssl/x509.h /usr/local/include/openssl/buffer.h \
/usr/local/include/openssl/paillier.h /usr/local/include/openssl/sm9.h \
/usr/local/include/openssl/rsa.h /usr/local/include/openssl/dsa.h \
/usr/local/include/openssl/dh.h /usr/local/include/openssl/sha.h \
/usr/local/include/openssl/x509_vfy.h /usr/local/include/openssl/pkcs7.h \
/usr/local/include/openssl/ecies.h /usr/local/include/openssl/sm3.h
BUG
src/bn_sm2p256.c当未定义 L_ENDIAN 时,编译的 BN 大数库有问题
参考链接
Karatsuba Algorithm (for fast integer multiplication)
OpenSSL密码库算法笔记——第1.2.2章 comba乘法